Deploy Smarter, Multi-Layered Threat Detection
Stop letting sophisticated threats slip through the cracks. Detect multi-stage TTPs & attack patterns with correlated threat scenarios.
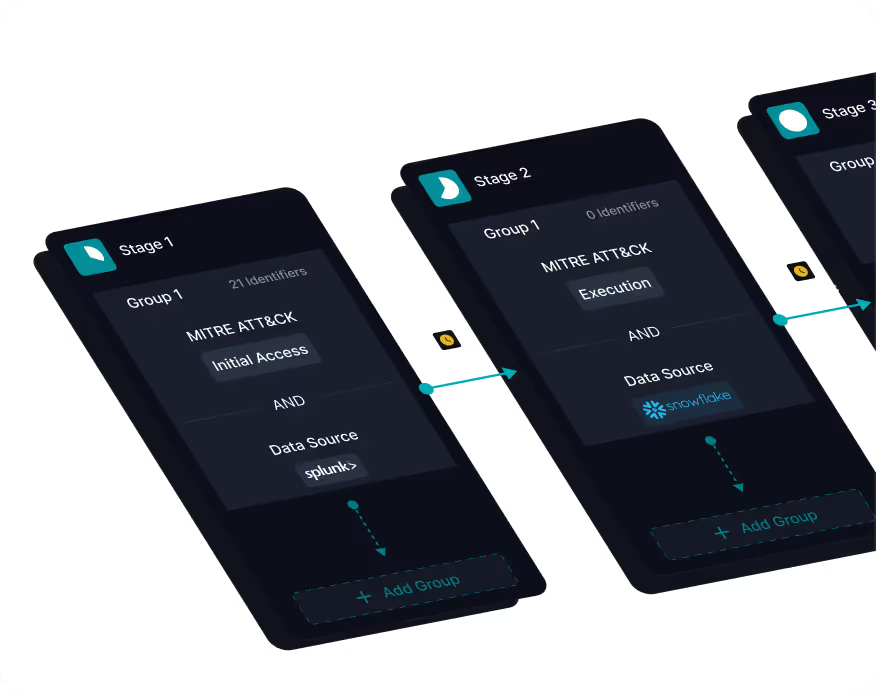









Elevate Your Detections to a New Dimension
Cross-Domain Correlations for Sophisticated Detections
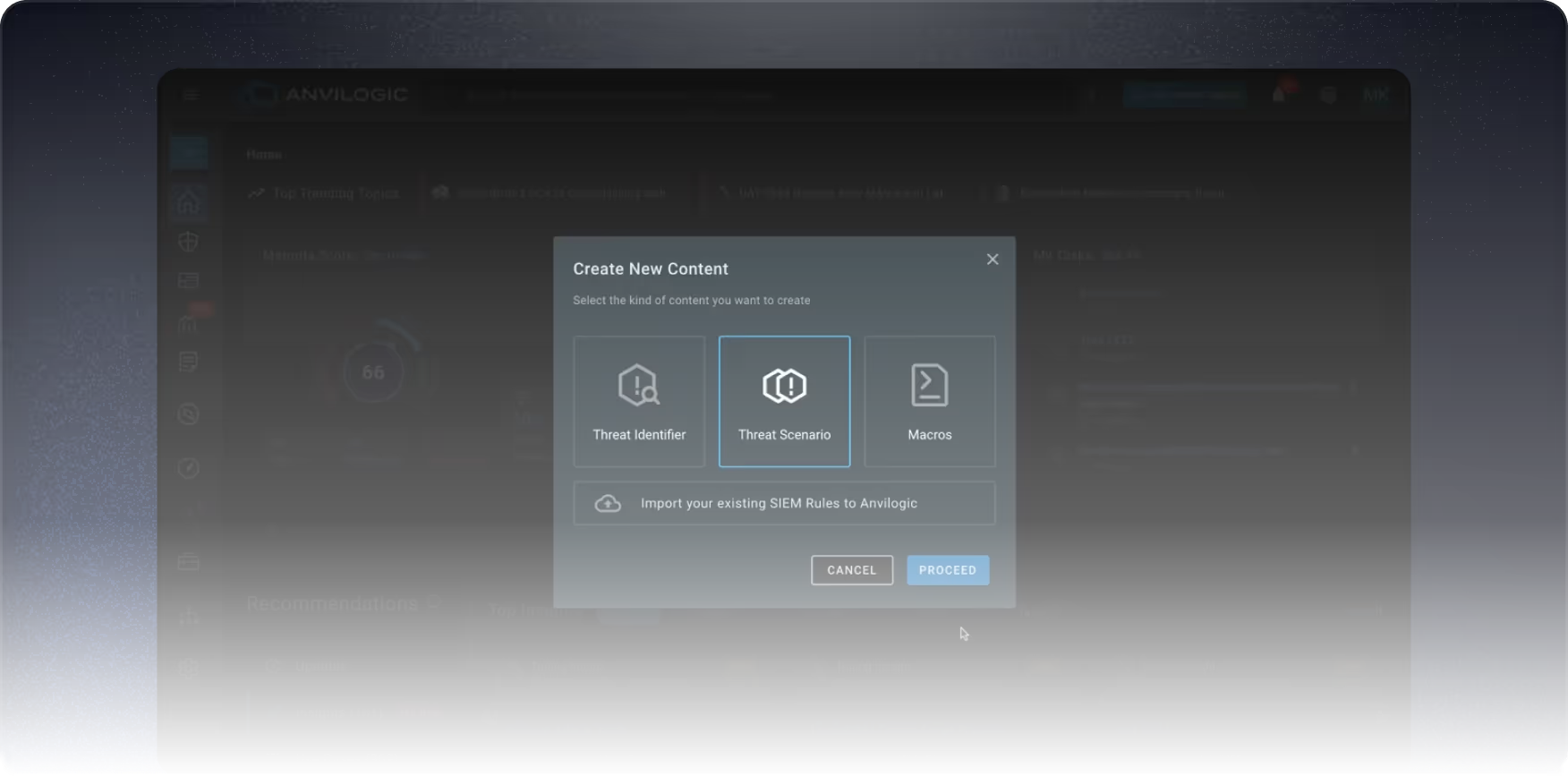
The Backlog is Real: Building sophisticated correlations is no small task. With a seemingly neverending backlog, it’s cumbersome, challenging, and sometimes impossible to do in large scale.
Simplified Correlation: Build advanced Threat Scenarios easily by threading your vendor alerts, queries, and intel-enriched detections on a drag-and-drop canvas. Map and tag correlations to MITRE ATT&CK and align your detections with industry standards for full kill chain coverage.
Cross-Platform Detection: Detect and hunt more effectively across multiple cloud platforms, data lakes, and log repositories, and bridge detection gaps without centralizing data.
No Rip-and-Replace: Deploy custom, correlated threat scenarios seamlessly alongside your current security stack, enhancing detection capabilities without disrupting your existing investments.
Activate Hundreds of Pre-Built Scenarios —or BYO Use Case
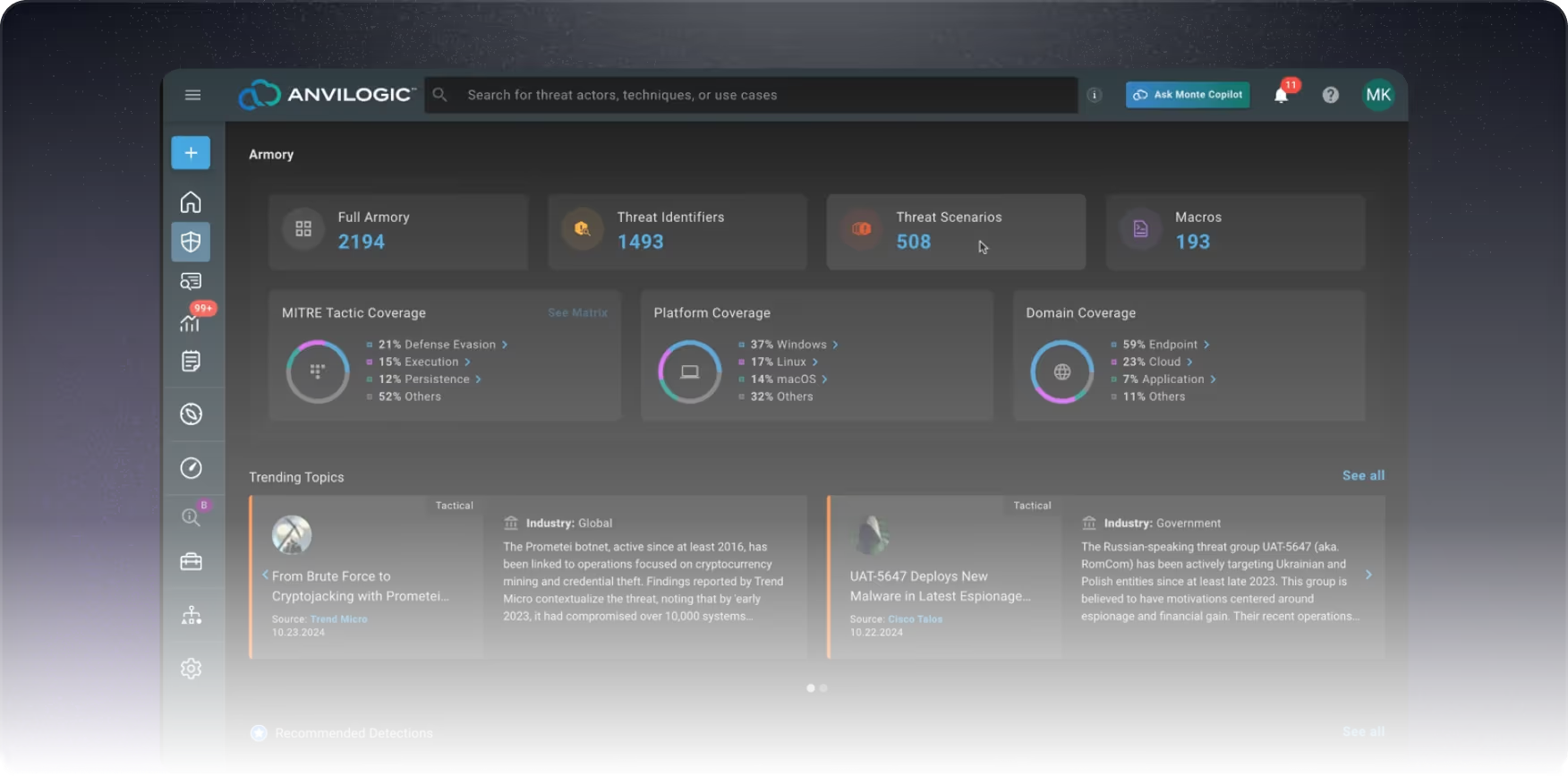
Ready-to-Deploy Threat Scenarios: Access hundreds of CI/CD-tested scenarios that are instantly deployable to match your tech stack, data platforms, and unique environment.
Smart Recommendations Catered to Your Tech Stack: Get tailored recommendations on which Threat Scenarios to deploy based on your tech stack, enabling rapid, optimized deployment.
Full Customizability: Start with pre-built scenarios, then modify, expand, or tailor them to match your specific requirements for maximum relevance.
Weekly Threat Report Updates: Stay up-to-date about the latest threats with new scenarios released each week and mapped to MITRE techniques, ensuring you’re covered against emerging risks.
A Low-Code Builder for Any Use Case
Built for Detection Engineers: Move beyond black-box vendor detections and create threat detection tailored to your unique environments and priorities in a true engineering workbench, free from the rigid constraints of typical SIEM and EDR solutions.
Detection-as-Code: With an intuitive drag-and-drop canvas, instantly generate complex correlation code that tackles your unique threats and delivers advanced detection precision at your command.
Transparent and Adaptable: Say goodbye to black-box detections and hello to complete visibility and control over your detection strategies, no matter your current or future state of security operations.
Maximize Your Investments: Implement a correlated narrative from detection to resolution without needing to centralize your data or ripping and replacing your existing investments.

Build Detections You Want, Where You Want







