Threat Informed Defense
Trade reactive tasks with proactive threat modeling with our threat prioritization framework, that aligns your detection efforts with your business and threat landscape, intelligently mapping out your unique attack surface for strategic defense.
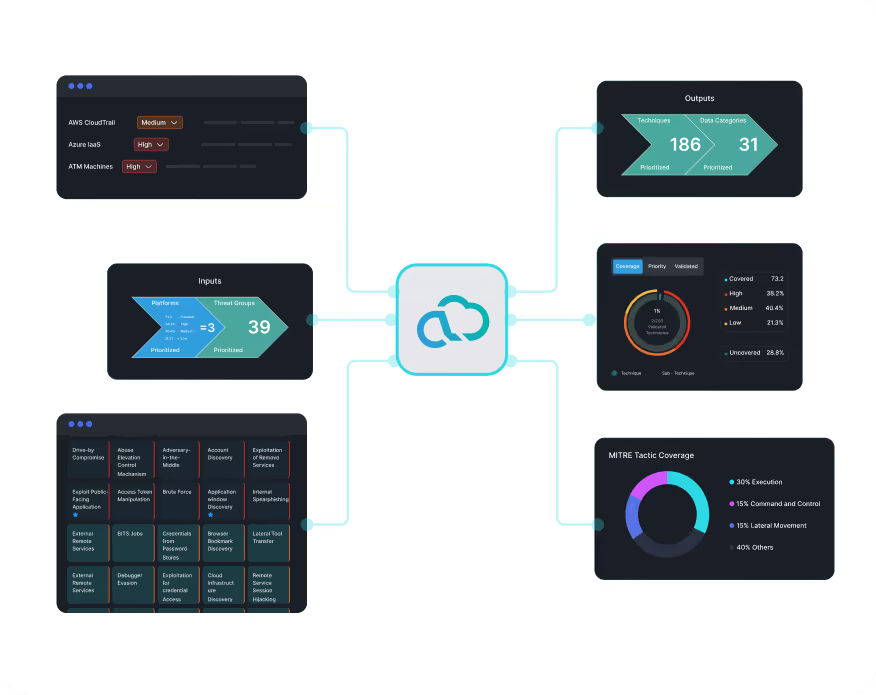









Not All Threats are Equal – Get Your Threat Priorities Straight
Blueprint Your Battle Plan for Precision Detection
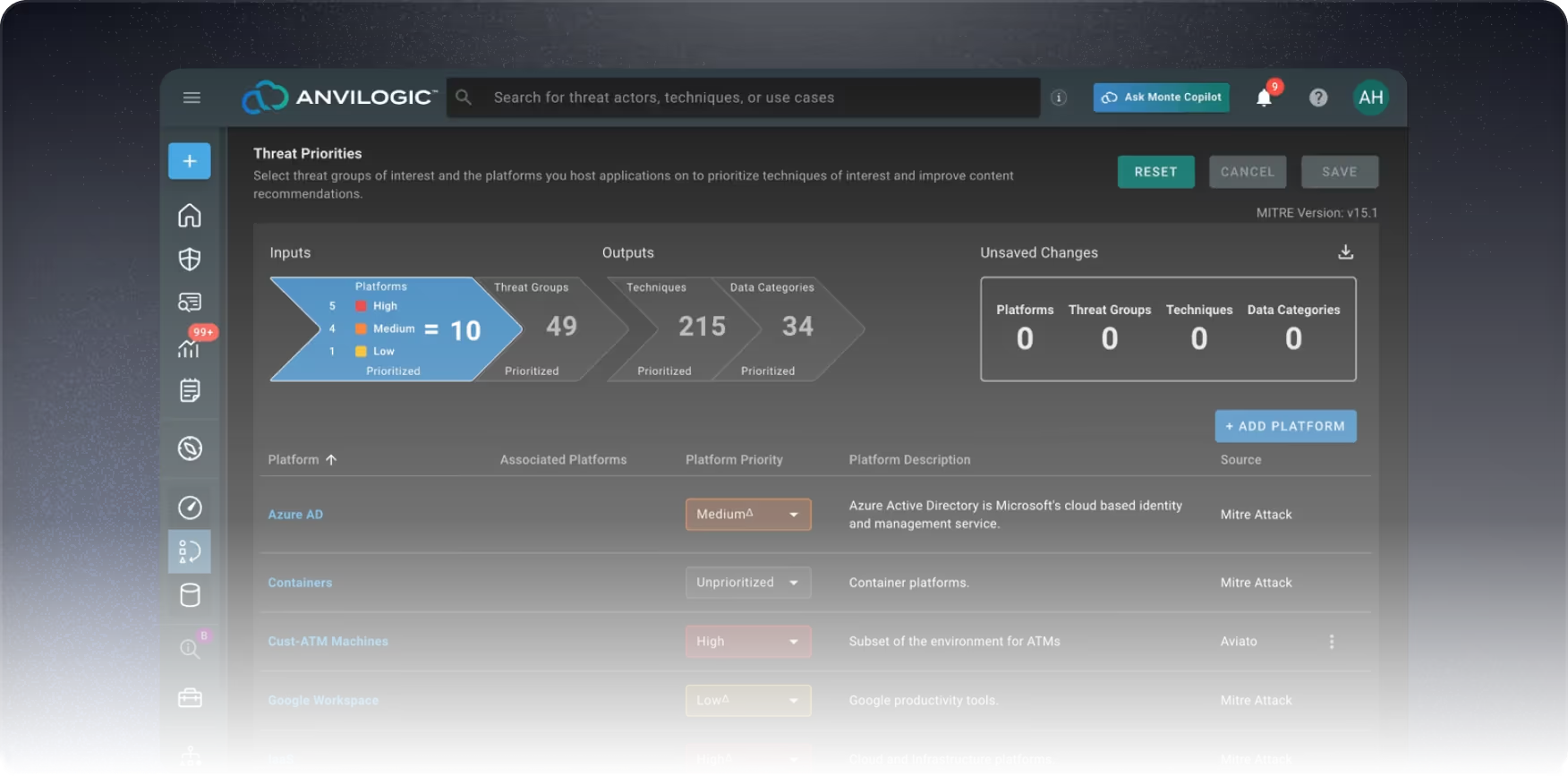
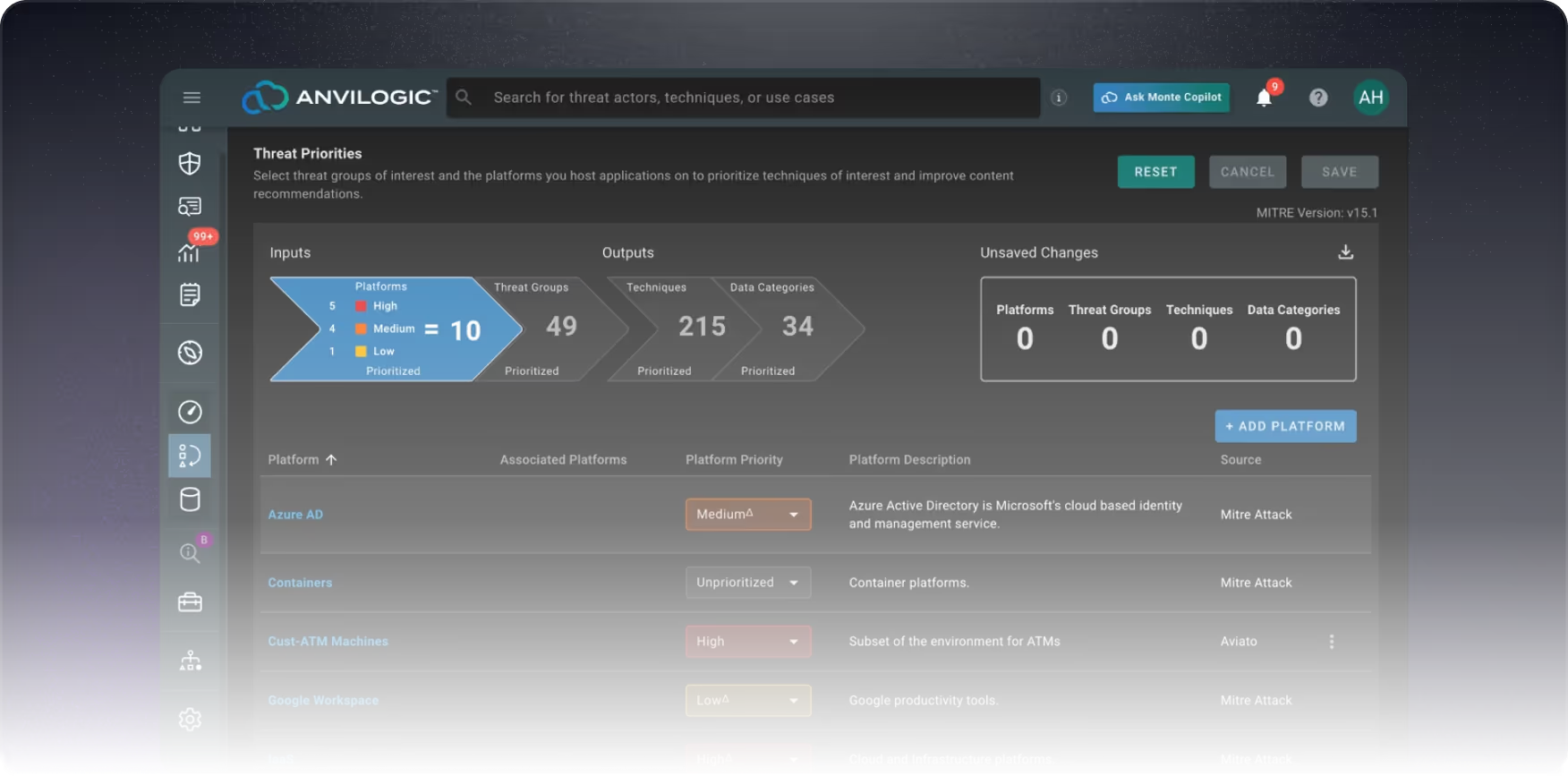
Define Your Inputs: Remove the need to manually map detection coverage to MITRE ATT&CK. Define critical assets and data feeds, and we’ll automate detection alignment tailored to your unique environment.
Own the Attack Surface: Set high, medium, or low priorities on platforms, add custom assets, and define their importance to provide essential inputs for our assessment exercise.
Curate Your Defense Plan: Customize your threat profile to your organization’s threat landscape, targeting threat groups relevant to your infrastructure, region, and industry.
Your Attack Surface, Your Rules: Seamlessly add new platforms and feeds as your environment evolves, with TTP-aligned detections automatically integrated into your Anvilogic deployment recommendations.
Targeted Threat Prioritization
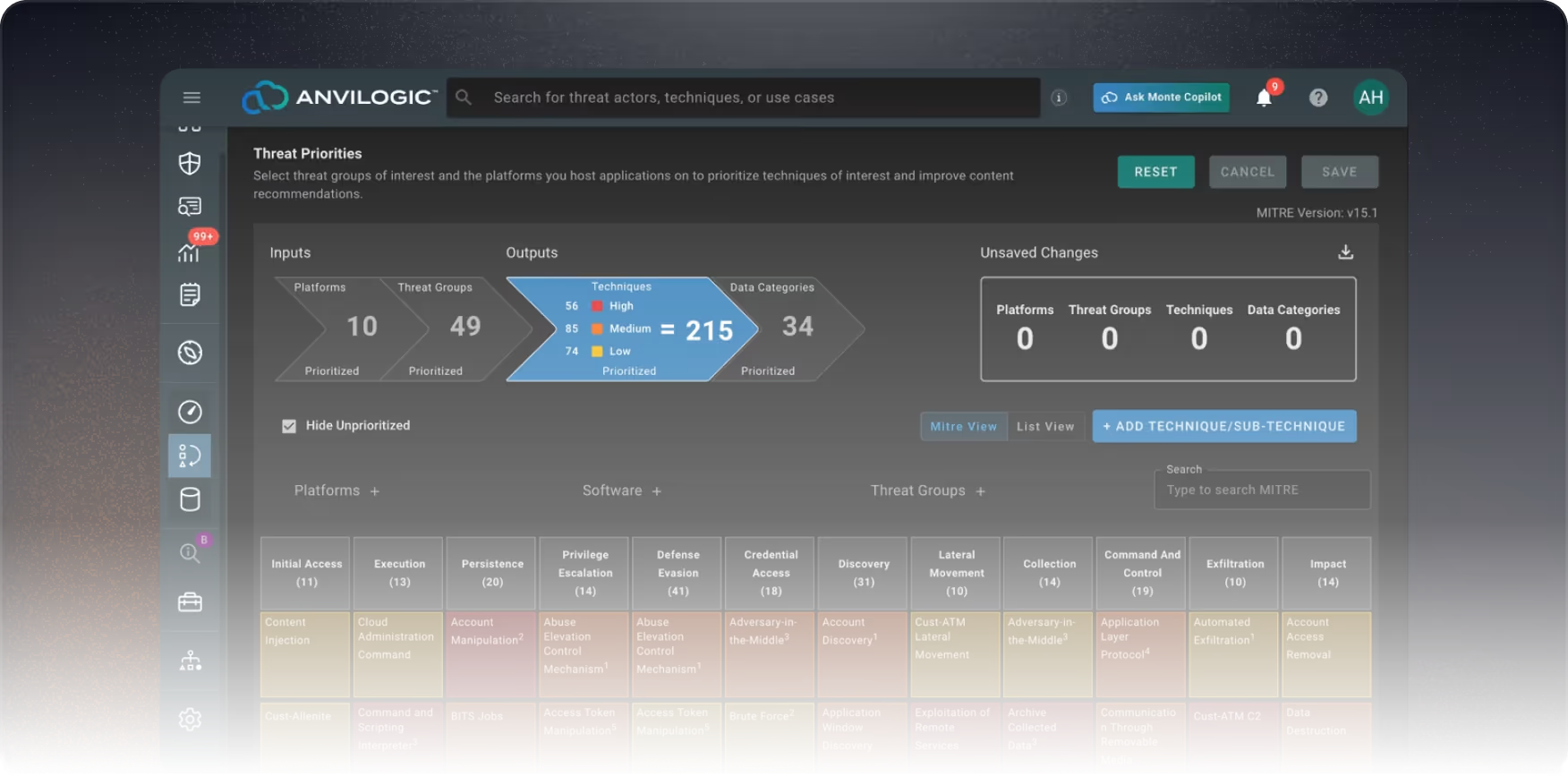
Pick Your APTs: Choose from an extensive list of threat groups sourced from our Threat Intelligence Library featuring behavioral and advanced TTPs from recent CTI reports and ATT&CK v16.
BYO Threat Campaign: Create your own threat groups and campaigns, mapping them to relevant data platforms and feed categories to assess and visually track your detection coverage and progress.
Hyper-Customized Threat Modeling: Gain a baseline assessment starting from day one with our platform goes beyond detection and technique coverage to assess your SOC operations.
The Devil is in the (Data Feed) Details: Achieve measurable success with insights and recommendations provided in our platform to build high-quality, effective detections.
Threat Modeling With Purpose 🤍
Play MITRE Chess, Not Bingo: Instead of superficially mapping ATT&CK coverage by checkmarks alone, effectively align your detection strategies across your hybrid ecosystem and measure how well they are correlated against your priorities and data feeds necessary to identify TTPs.
Map Your Coverage With Impact: Easily visualize your detection coverage across your attack surface to identify validated coverage and uncover gaps within your current environment for each defined threat priority, informed by your data platforms and feeds.
Actionable Visualization With Integrated Health Checks: Instantaneously spot inactive and unhealthy feeds to keep their ability to detect rules in check.
Continuous Improvement: Easily update threat priorities and data inputs as your environment shifts, keeping your coverage sharp and responsive.

Build Detections You Want, Where You Want







