Modern Detection, Smarter Triage Anvilogic for Splunk





The World's Best SOC Teams Use Anvilogic
Triage, Tune, Detect Smarter—without ES
Build SPL Detections in Minutes,Without Being a Splunk Ninja
Move from risk-based to behavioral-based detections with our Low-Code Detection Builder to create complex yet customizable detections focused on attack patterns for increased accuracy and improved coverage.
Correlate multi-stage attack sequences using our Custom Detection Builder, streamlining advanced SPL with Detection-as-Code and enabling high-impact and high-fidelity detections.
Access thousands of out-of-the-box SPL detections in our ever-growing detection library that can be easily deployed and customized to your unique threat priorities.
Relieve yourself of the less-than-fun detection engineering management tasks with automatic MITRE ATT&CK mapping, version control, custom tagging, integrations, and more so you can return to high-impact tasks.
Close Detection Coverage Gaps
Easily import your Splunk rules and automatically map them to MITRE ATT&CK to visually assess your detection coverage, identify coverage or data source gaps, and refocus efforts.
Augment your detection efforts with our library of out-of-the-box rules, tested and validated by our purple team, and our AI Copilot that suggests new detections to deploy to Splunk.
Leverage the Anvilogic platform to create threat models customized to your risks, using information such as your industry, infrastructure, assets, and regions.
Utilize our Detection Engineering Workbench, equipped with advanced version management and control features, to easily tag, enrich, and track the evolution of your detections.
ML-Driven Optimization of Your Splunk Rules
Stay ahead of detection fine-tuning and maintenance by leveraging predictive and generative AI and machine learning (ML) models to deliver thoughtful recommendations unique to your environment.
Force-multiply your team with AI-generated insights that continuously monitor data feed health, flag suspicious activity, and provide allowlist suggestions to tune noisy rules.
Get how-to guidance from Anvilogic’s Copilot, exclusively trained by SOC personas, on correlating your detection output into behavior-based threat scenarios that create better detection outcomes.
Let predictive and generative AI do the tedious work by automating the detection engineering lifecycle so you can get back to doing high-value activities.
AI-Assisted Triage to Cut 45% Alert Noise, with 98% Confidence
Context That Cuts Through the Noise: Every alert is enriched with entity, identity, and system-level context — and AI-prioritized based on scenario relevance, threat score, and asset criticality.
Precision Responses, When It Matters: Trigger downstream action in Torq, Tines, or any SOAR only when signals are strong — and always with full context and explainability.
L1 Triage on Autopilot: Reconstruct alert timelines and generate investigative queries to accelerate decision-making with enriched, actionable context without the manual digging.
Real Results, Proven at Scale: A global financial firm cut alert volume by 45% and saved 71 hours/day using our AI triage analyzer agent. Learn More
How Anvilogic for Splunk Works
Access thousands of pre-built, validated SPL detections from our Detection Armory to strengthen your Splunk coverage and accelerate D&R. Our AI SOC platform goes beyond just rule library + building detections + tuning, it automatically recommends and deploys the right detections, links related alerts into multi-stage threat scenarios, and filters out false positives with high accuracy. All alerts flow into a triage and investigation workspace, where you can see correlated activity across tools, understand attack paths, and prioritize real threats.
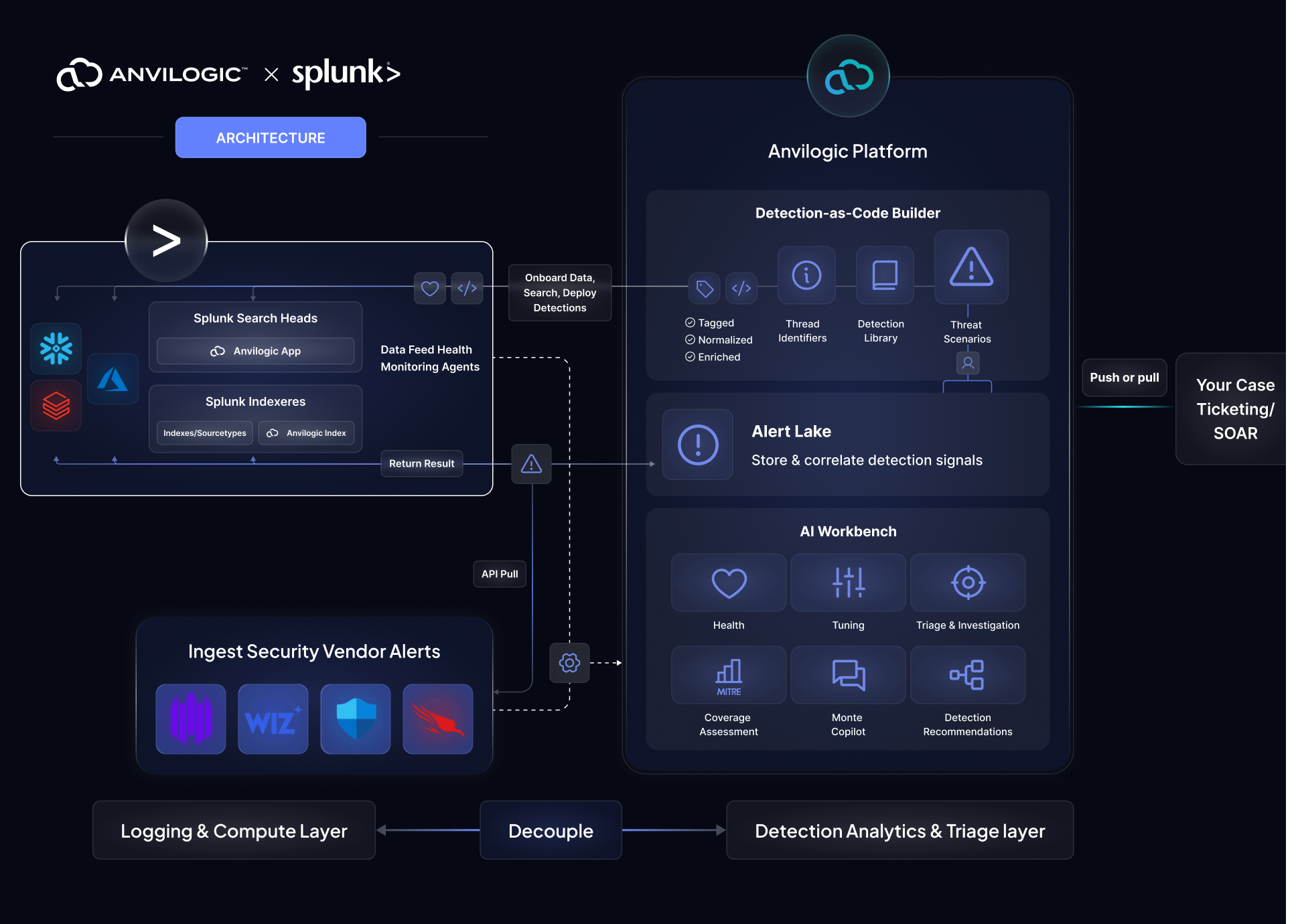
Anvilogic + Splunk
The AI SOC Layer For Splunk










.svg)

.svg)









.svg)

.png)


