By: Kevin Gonzalez, VP of Security, Operations, and Data at Anvilogic
Detection engineering has always felt like that third-grade science fair project—you know, the one where you banged your head against a foam board until something resembling the scientific method emerged. You observe potential threats, question whether they've already compromised your environment, hypothesize detection approaches, experiment with logic, analyze results, adjust, experiment again, analyze, adjust... and repeat until you either succeed or succumb to existential dread.
The problem? This iterative cycle is not only time-consuming but demands extensive research and deep technical understanding across systems, cloud platforms, applications, and network engineering. For junior analysts especially, it's a perfect storm of complexity: unfamiliar data schemas, limited threat context experience, and unknown detection engineering processes. The result is often detection logic that either doesn't work, casts too wide a net, or misses critical threats entirely.
But what if we could compress those painful iteration loops and automate the scientific method itself? What if an AI agent could be your detection engineering partner, staying five moves ahead of your process while maintaining production-grade standards from day one?
The Current Detection Engineering Reality Check
Manual tasks consume hours each day—time working against detection engineers who are responsible for managing the detection lifecycle across numerous detections, according to recent industry research. Teams are stuck in a tightrope act, crafting rules precise enough to catch real threats while staying flexible enough to detect a wide range of techniques.
Think about the typical detection engineering workflow. An analyst spots a new attack technique in a threat report, spends hours researching the technical details, fumbles through data schema documentation, writes initial detection logic, tests it against production data, discovers it's either too noisy or too narrow, tunes it repeatedly, documents the use case, and then finally deploys to production weeks later.
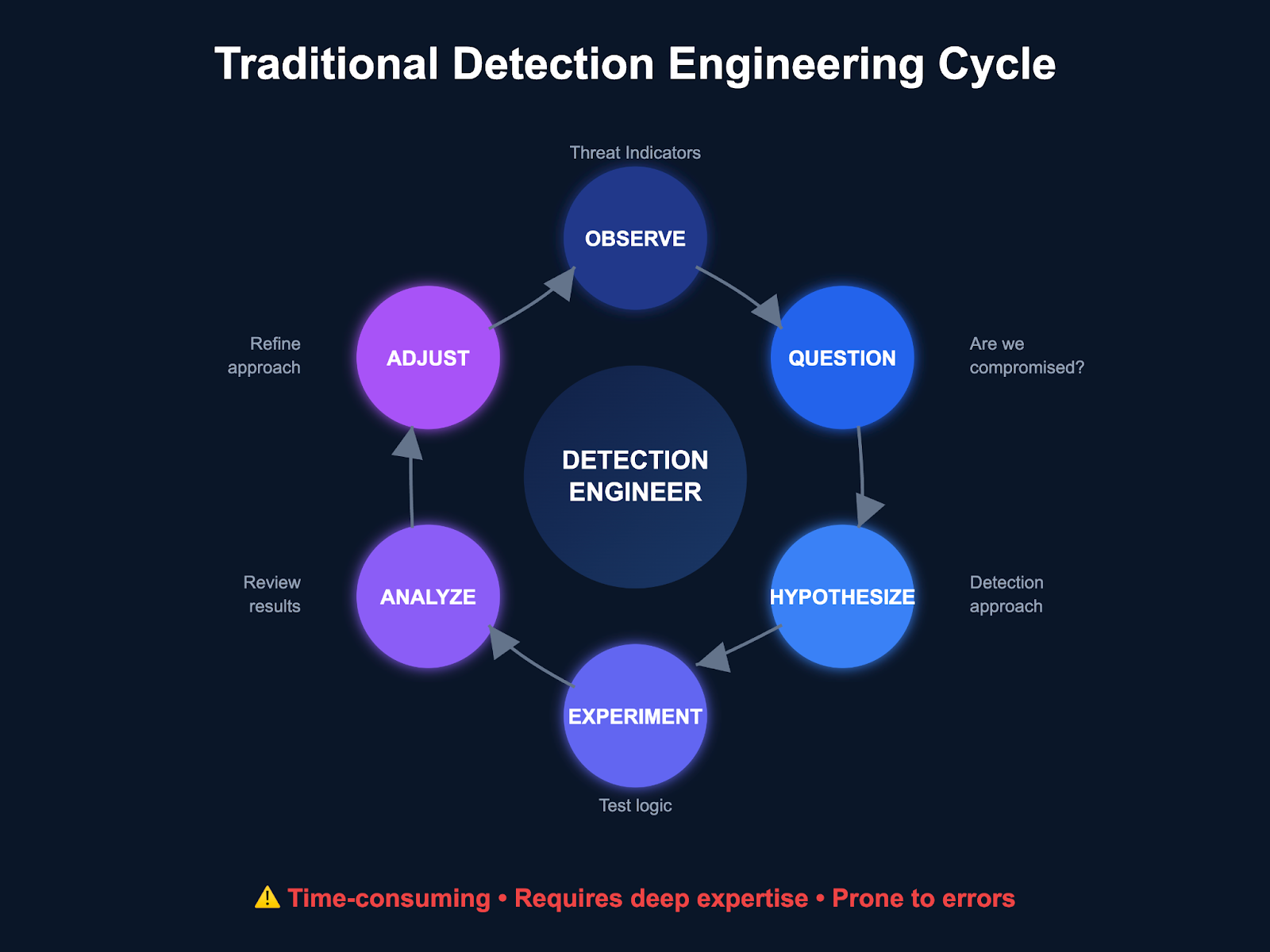
Time Consuming Detection Loop
Now multiply that across hundreds or thousands of detections your SOC needs to maintain. Teams are getting tangled in manual processes across multiple tools and UIs, with cumbersome maintenance slowing down detection deployment and updates.
The traditional approach treats each detection as a standalone project rather than leveraging the collective intelligence of your existing detection arsenal and organizational knowledge base.
Enter Agentic Detection Engineer
It’s 2025 and AI in cybersecurity is already quickly moving from chatbots to a more agent-driven approach, and agentic AI is expected to accelerate Security Operations Center (SOC) automation. AI agents could soon work alongside humans in a semi-autonomous manner to identify, think through, and dynamically execute tasks such as alert triage, investigation, response actions, or threat research.
An agentic detection engineering system doesn't just automate individual tasks but also compresses the entire scientific method into minutes while maintaining production-grade quality. Here's how it works:
Foundation: Proper Detection-as-Code Infrastructure
Before any agent can effectively build detections, you need a solid foundation: defined data structures, repeatable components, and exemplary content that serves as a blueprint for new detections. This is essential for the agent to understand what "production-ready" means in your environment.
The agent leverages Retrieval-Augmented Generation (RAG) across three critical knowledge bases:
- Data Schema Documentation: Understanding your raw data structures, field mappings, and available telemetry
- Existing Detection Library: Your organization's current detection arsenal and their patterns
- Curated Threat Intelligence: Indexed external sources and threat research
The Five-Move Approach
Here's where agentic detection engineering gets interesting. Instead of starting with basic logic and iterating toward production quality, the agent begins with the end state in mind.
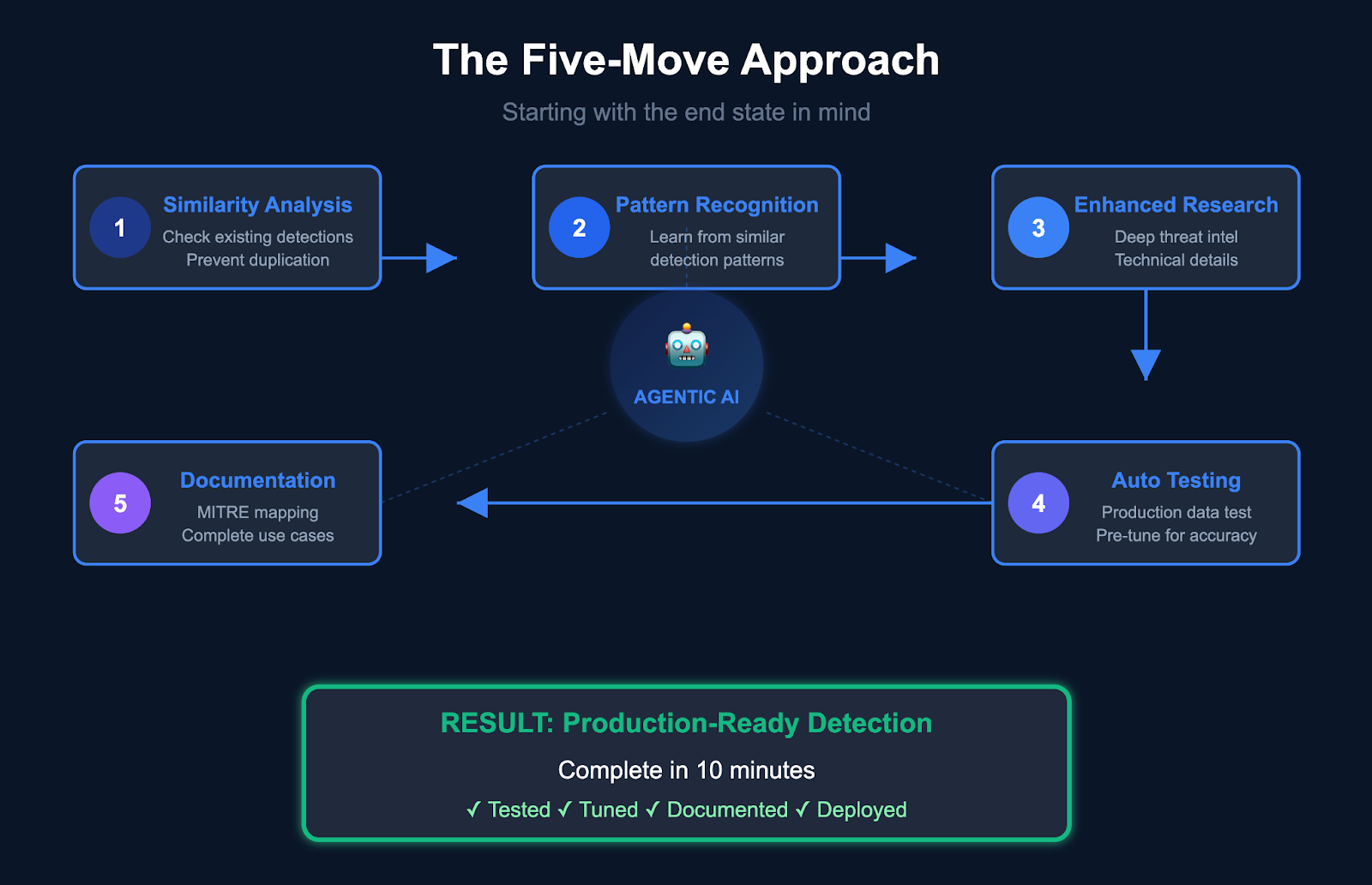
Move 1: Similarity Analysis Before writing new logic, the agent analyzes your existing detection library. Is this duplicated effort? Can an existing rule be modified to accommodate both requirements without breaking documented use cases? This prevents detection sprawl and maintains consistency. (Worth noting that this is a painfully boring and time-consuming process for us humans.)
Move 2: Pattern Recognition Even if nothing directly matches, the agent identifies structurally similar detections. It understands how to approach process execution monitoring, network connection analysis, or file modification tracking based on your organization's established detection engineering patterns.
Move 3: Enhanced Research Integration Here's where the magic happens. The agent doesn't just research the basic threat, it dives deep into indexed man pages, technical documentation, and threat intelligence to understand nuanced implementation details.
For example, if you ask for "SSH executions on endpoints with config files in temp directories," the agent doesn't stop at basic process monitoring. It discovers that the -F flag specifically indicates config file usage and automatically incorporates temp directory paths into the detection criteria. You get production-grade logic that's already several iterations ahead of where you'd start manually.
Move 4: Automated Testing and Pre-Tuning The agent runs automated tests against your data, identifies potential false positives from legitimate activities (like developer tools or admin operations), and builds appropriate allowlisting into the logic before you ever see it. No more deploying detections only to discover they're flooding your SOC with alerts.
Move 5: Complete Documentation By the time the detection reaches you, it includes comprehensive documentation: purpose, approach, enrichment factors, MITRE ATT&CK mappings, applicable threat groups, and any tuning decisions made during testing.
Real-World Implementation: The SSH Loading Configs Example
Let's see this in action. You provide the natural language request: "Please find executions of SSH on endpoints with a config file in a temp directory."
Traditional approach: You'd start with basic process monitoring for "ssh.exe," realize you need to filter for config files, research SSH command-line options, discover the -F flag, manually add temp directory checks, test against production data, discover noise from DevOps tools, add exclusions, and document everything—probably taking days or weeks.
Agentic approach in minutes:
- Analysis: No existing SSH Windows detections, but multiple process execution detections available as templates
- Research: Agent indexes SSH documentation, discovers -F flag for config files, identifies common temp directory paths
- Logic Creation: Builds detection monitoring process creation where process name contains "ssh" AND command line contains the "-F" flag AND file path includes temp directories
- Testing & Pre-Tuning: Runs against recent data, identifies benign DevOps activities. Adds allowlisting for known development tools and CI/CD processes
- Documentation: Generates complete use case documentation with MITRE T1021.004 mapping and threat group associations
Result: Production-ready detection that's already been tested and mostly tuned, complete with documentation explaining every decision. A skilled human still needs to check the logic and finalize the tuning, but the amount of work needed to get to that point has been cut dramatically.
The Compound Effect: Beyond Individual Detections
The successful implementation of Agentic AI in cybersecurity hinges on two critical factors: accuracy and transparency. By clearly demonstrating the reasoning process, planned steps, and systems engagement, this transparency creates effective human-AI partnerships where humans maintain oversight while the AI handles structured, repetitive tasks at scale.
The real power emerges when you consider the compound effect across your entire detection engineering program:
Consistency at Scale: Every detection follows your organization's established patterns and standards automatically. No more style guides or training on detection formatting—the agent enforces consistency inherently.
Institutional Knowledge Capture: Each detection becomes part of the agent's learning corpus, improving future outputs. Your organization's detection engineering expertise becomes cumulative and transferable.
Research Acceleration: AI will augment human work more in the coming years. The agent automatically performs the research that typically consumes hours of analyst time—threat report analysis, ATT&CK framework mapping, command-line documentation review, and environmental context gathering.
Quality Assurance Built-In: Testing and tuning happen before human review, not after deployment. This prevents the alert fatigue that comes from deploying untested detections.
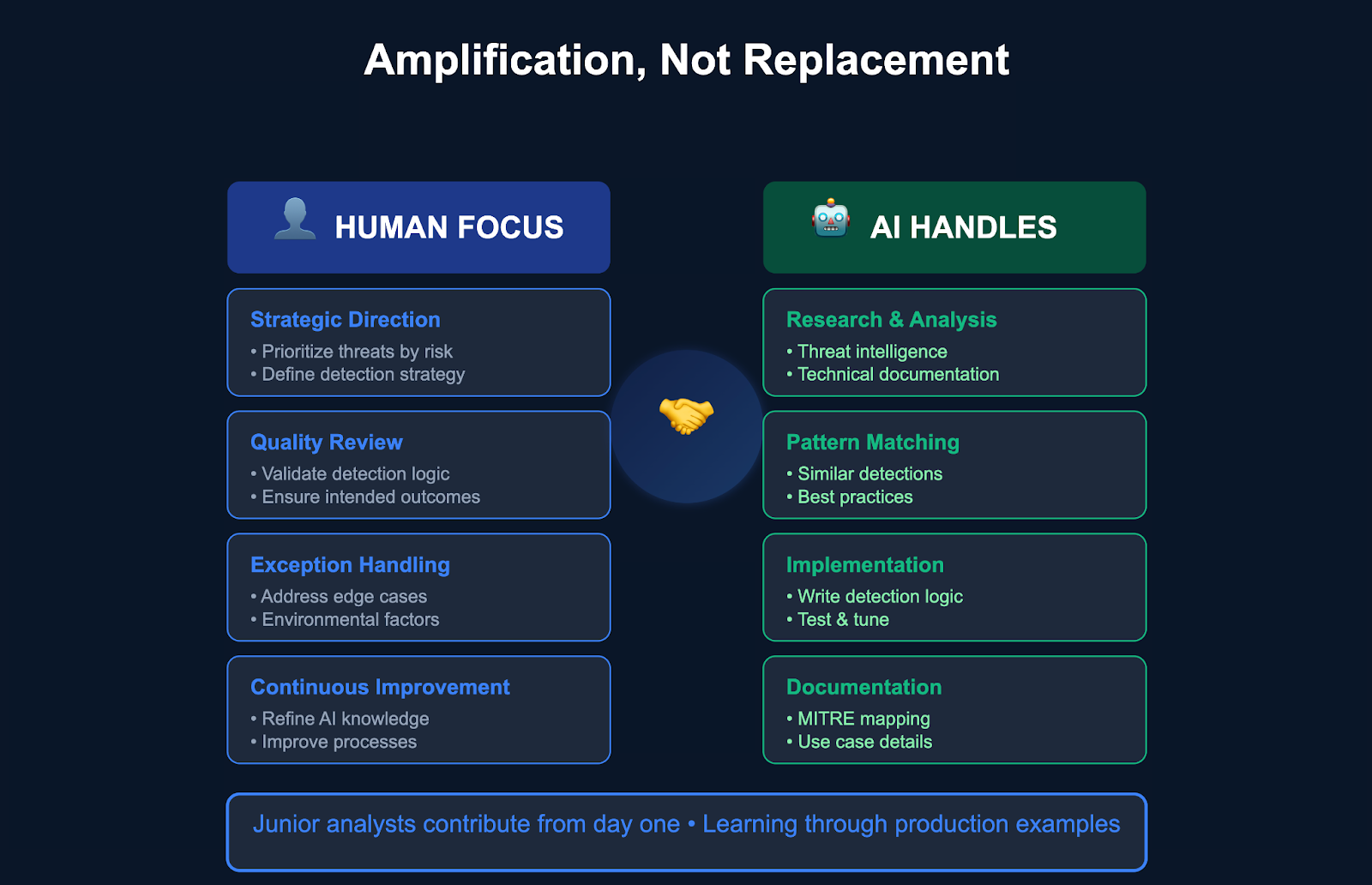
The Human Element: Amplification, Not Replacement
The goal isn't to automate everything instantly, but to build confidence with agent-based workflows that can evolve with your team's growing expertise. Agentic detection engineering amplifies human expertise rather than replacing it.
Detection engineers shift from writing individual rules to orchestrating detection strategies. They focus on threat modeling, architecture decisions, and exception handling while the agent handles the mechanical implementation. Junior analysts can contribute meaningfully from day one, asking natural language questions and receiving production-grade outputs that teach them organizational and detection engineering standards through example.
The human remains essential for:
- Strategic Direction: Determining which threats to prioritize based on organizational risk
- Quality Review: Final validation that detection logic aligns with intended outcomes
- Exception Handling: Addressing edge cases and complex environmental factors
- Continuous Improvement: Refining the agent's knowledge base and decision-making processes
Implementation: Building Your Agentic Foundation
Organizations considering agentic detection engineering should focus on three foundational elements:
1. Data Foundation Ensure your data schemas are well-documented and accessible. The agent's effectiveness depends entirely on understanding what data is available and how it's structured. This isn't just about having documentation—it's about having accurate, up-to-date, and comprehensive documentation.
2. Content Curation Build a library of exemplary detections that represent your organization's quality standards. These become the training examples that teach the agent how to maintain consistency with your existing practices.
3. Research Integration By leveraging advanced process mining tools, AI and IA technologies, companies can gain deep insights into their operations, enabling data-driven decisions that enhance efficiency. Index your trusted threat intelligence sources, technical documentation, and organizational knowledge base. The agent's research capabilities are only as good as the sources it can access.
The Security Implications: AI Defending Against AI
As AI quickly advances cyber threats, organizations seem to be taking a more cautious approach, balancing the benefits and risks of the new technology while trying to keep pace with attackers' increasing sophistication. The reality is that AI technology makes it easier and faster for cybercriminals to carry out cyberattacks, effectively lowering the barrier to entry for some actors and increasing the level of sophistication of established players.
This creates an arms race where defense must evolve at the same pace as offense. It’s well within the realm of possibility that, in the future, we'll move past simple AI-driven threat detection into full-scale machine-versus-machine warfare.
Agentic detection engineering becomes not just an efficiency improvement but a strategic necessity. When attackers can generate new variants and bypass techniques automatically, defenders need detection engineering that can iterate and adapt at machine speed.
Looking Forward: The Evolution of SOC Operations
Analysts become prompt engineers and agent supervisors. Security managers act more like threat architects, mapping adversary behavior and curating AI guardrails. SOCs will no longer grow in size, but explode in leverage—fewer people, more autonomy.
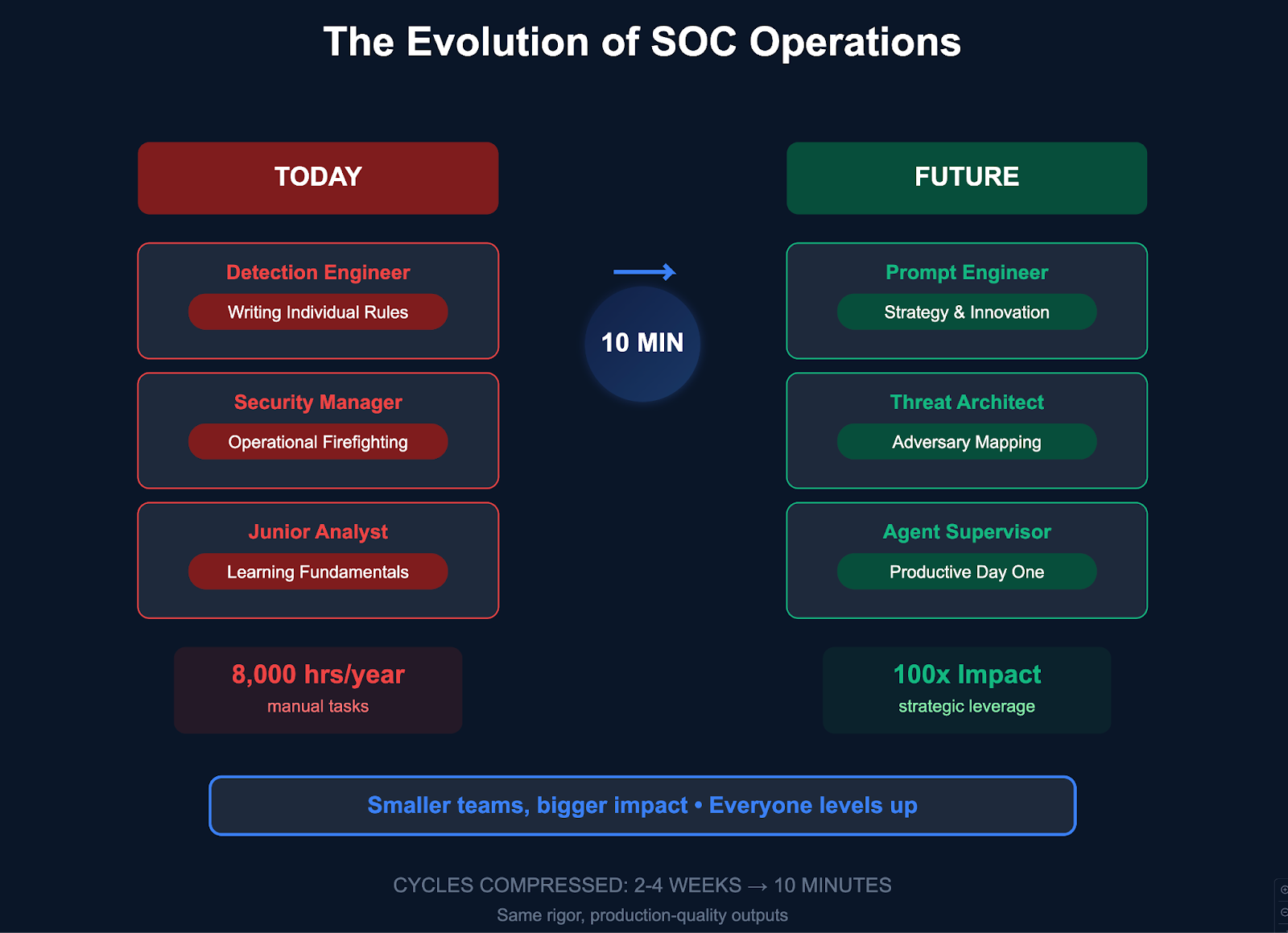
The future SOC doesn't eliminate human expertise but rather multiplies its impact. A few detection engineers working with agentic systems can maintain detection coverage that previously demanded entire teams. Junior analysts can contribute from day one, learning through interaction with systems that embody senior-level expertise.
This transformation delivers massive time dividends: detection engineers reclaim 99.8% of their time previously spent on research, documentation, and iterative testing. Instead of burning weeks researching threat reports and tuning false positives, they redirect those hours toward strategic threat modeling, advanced hunting operations, and designing sophisticated correlation rules that span entire attack chains. The scientific method remains intact—we've simply automated the mechanical execution, freeing human creativity for the complex analytical work that truly requires expertise.
Embracing the Agentic Advantage
Detection engineering has always been a race to out-innovate adversaries who constantly tweak their tactics. AI and automation are already closing that gap, and nearly everyone in the field agrees these technologies will redefine detection work in the next few years. The first to reap the benefits, however, will be the teams that have already laid a rock-solid foundation: clear schemas, well-documented logic, and repeatable processes. With that groundwork in place, they can inject AI straight into structured data and proven workflows, turning automation into an early-mover edge rather than a science experiment.
The organizations that thrive will be those that augment their detection-engineering muscle with agentic systems—not to replace human expertise with them. When an agent can research threats, map the right data structures, write production-grade logic, test against real logs, pre-tune for environment quirks, and generate full documentation in minutes, you’re not just saving time, you’re redefining what’s possible in cybersecurity.
The scientific method that has propelled discovery for centuries isn’t going away. We’re simply giving it the speed and scale required to keep pace with modern threats.
Ready to compress your detection-engineering timeline from weeks to minutes? The agentic revolution isn’t coming, it’s already here. The only question is whether you’ll lead the charge or play catch-up.



.svg)







.png)



.svg)








