AI Agents
for the Modern SOC
Automate the Repetitive. Accelerate the Strategic.

A Smarter Operating Model for Cost Efficient Threat Detection & Response Built for Hybrid Reality
We introduce our version of an AI SOC: an adaptive platform that meets you where you are, and abstracts the detection and triage layer from where data resides. This is the result of our long-standing investment in its detection engineering & orchestration of scheduling, of how logic is built, tuned, and scaled.
It’s designed to solve a tradeoff every SOC team knows all too well: How do you cast a wide enough net to catch all relevant attack patterns without overwhelming your team with noise?
In practice, most teams lean toward narrowing detections.
Not because it’s the best approach
But because it’s the only way to stay above water.
That’s the real constraint: human capacity.
And it shapes everything: from how detections are written to how pipelines are built.
The pressure compounds across your SIEM and wrangling budget x coverage.
Our AI SOC shifts that constraint with a suite of intelligent agents that are detection-literate and are specially designed to augment every stage of the detection lifecycle—from the onboarding of the logs themselves throughout the maintenance and triaging of the resulting alerts.
These aren't bolt-on chatbots, they’re trained on real-world adversary behaviors, telemetry schemas & patterns, and thousands of detections to deliver contextual, continuous intelligence that doesn't just generate responses, they generate results.
AI Agents Across the SecOps Lifecycle, Your Stack
Most security platforms apply AI at a single step — usually alert triage — without solving the root issues across detection engineering, tuning, and investigation. Anvilogic takes a different approach.
We embed AI agents across the entire detection lifecycle, automating the manual, repetitive work detection engineers and SOC analysts wrangle with every day. The Anvilogic AI system leverages a combination of proprietary tools and external connectors to power these SecOps workflows.
Our AI Workflows aren’t tied to one platform, we can run them on top of & in any combination of Splunk, Microsoft Sentinel, Snowflake, Databricks and more.
With Anvilogic, you’re never locked in. You gain the flexibility to adopt, expand, or replace technologies on your own terms, without losing detections or operational momentum.
Triage Only



.svg)



.svg)



.svg)
.svg)





Coverage
Context by Design
Context-driven triage, not noise, not hallucination.
Detects real adversary behavior, not just matching alert strings.
Collaboration with Guardrails
No overfitting — robust to real-world noise
Maintains fidelity across SIEMs, clouds, and data lakes
Trustworthy results at scale
Fast to deploy, little setup. Consistent outputs across sources.
Prevents "cross-thread bleeding" by anchoring triage in logic, not logs
Works with, not replaces
Transparent reasoning logic that analysts can follow, enabling human-in-the-loop decision-making


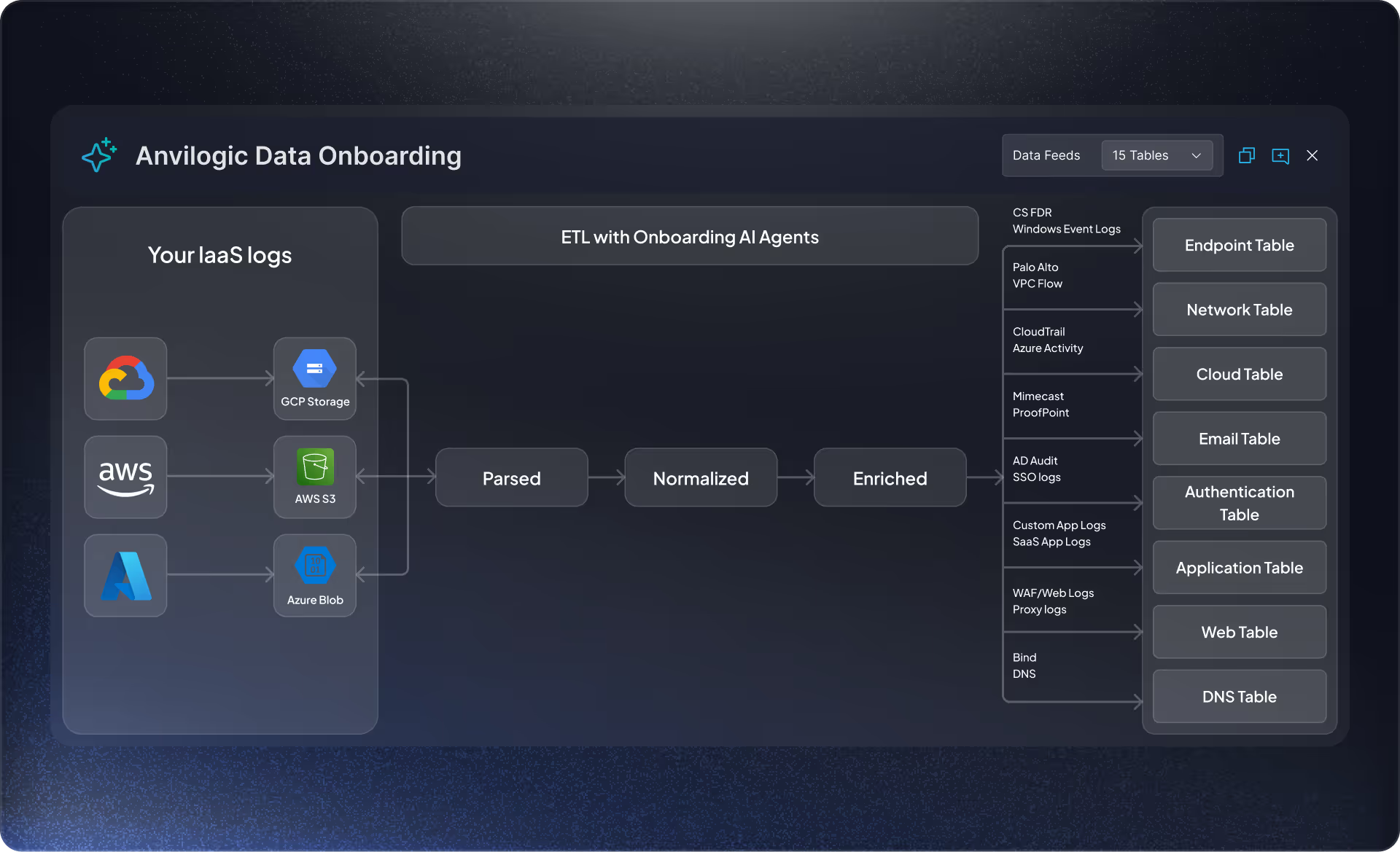
Data Onboarding Agents
Now with Anvilogic, you can...
Enrich logs with context variables and tagging
Ensure data quality across diverse cloud storage (S3, Blob, GCP)
Make security data usable by both SOC and data teams
Case Study: Alteryx

Alteryx turned to Anvilogic to accelerate detection engineering, streamline investigations, and gain better control over security costs.
With Anvilogic, the team:
- Reduced time-to-value for detection use cases with a visual, low-code builder, now accelerated even further by an agentic chat experience that guides detection creation from idea to deployment
- Decoupled detection from storage, giving them greater budget flexibility and cost control
- Streamlined investigation workflows with unified search across all connected data sources
- Assessed and improved detection maturity through native MITRE ATT&CK alignment and coverage tracking
Detection Engineering & Hunting Agents
Now with Anvilogic...
Natural Language to SQL Translation
Converts security questions into SQL, SPL, KQL queries
Understands context from your environment's schema
Handles complex filtering and time-based queries
Environment Awareness
Knows your data sources and existing detections
Leverages Gold tables for trusted data access
Understands our Rule Library content and threat intelligence
Query Optimization
Generates efficient SQL for large-scale data searches
Automatically applies appropriate time windows
Optimizes joins and filters for performance
Detection-as-Code Generation
Converts queries to our modular framework
Preserves query logic and filters
Optimizes for performance across data platforms
Maintains detection accuracy through transformation
Intelligent Documentation & Metadata Generation
Auto-generates descriptive names and summaries
Auto-maps to MITRE ATT&CK tactics and techniquesIdentifies associated threat groups
Assigns appropriate kill chain phases
Calculates impact scores and severity levels
Suggests detection categories and tags
Context Preservation
Carries forward search context and intent
Includes relevant threat intelligence
Documents detection logic and purpose
Works with all supported data repositories: Splunk, Azure, Databricks, Snowflake
Seamless analysis across different data platforms
Pattern Recognition
Analyzes alert fields to find repetitive benign patterns
Groups similar events by common attributes (users, IPs, processes)
Calculates frequency and distribution of field values
Statistical Analysis
Applies statistical thresholds to identify outliers vs. noise
Measures alert volume trends and spikes
Calculates noise reduction impact of proposed filters
Intelligent Allowlisting Recommendation
Generates allowlist candidates based on alert patterns
Cross-references with threat intelligence to avoid false allowlisting
Provides confidence scores for each suggestion
Iterative Tuning Workflow
Add allowlist entries one at a time to see incremental impact
Continue tuning until desired alert volume is achieved
Test impact before deploying to production
Works on both deployed and undeployed use cases
When to use it:
New detection validation - Before deploying to ensure minimal false positives
Alert fatigue - When repetitive benign alerts overwhelm your team
Detection maintenance - Regular reviews to optimize existing detections
Post-incident cleanup - After identifying false positive patterns during investigations
Outcome: Build detections 3x faster, with 90% fewer false positives.
Your SecOps in 5X
Let’s break down the benefits by role.
SOC Teams
- Automatically triage alerts with AI-powered verdicts (malicious, suspicious, benign)
- Focus on real threats with noise filtered pre-investigation
- Use chat-based agents to build, tune, and ship detections faster with less manual effort
- Reduce burnout by automating repetitive tasks like enrichment and evidence stitching
- Supports natural language queries across all data sources
- Enables security operations beyond basic data querying
Security Architects
- Automate detection tuning and correlation logic without maintaining multiple rule languages
- Normalize detection pipelines across hybrid infrastructure
- Enable hybrid/multi-cloud coverage without data centralization
- Standardize logic across business units and cloud tenants
- Augment existing SIEM initially rather than immediate replacement
- No disruption to existing security operations
- Supports full SIEM migration with automated detection conversion
CISOs & Security Leaders
- See measurable impact: AI-driven triage cut alert volume by 45% and saved 71 analyst hours/day
- Free your team from repetitive triage and maintenance
- Quantify detection ROI and reduce reliance on vendor content
- Reduce detection debt
- Shift detection from expense center to strategic differentiator
Triage & Investigation Agents
Now with Anvilogic.....
alerts
suspicious
unusual,
or benign
Selective analysis rules to define which alerts should be automatically analyzed
Manual re-run capability to trigger analysis on-demand
Status indicators showing when analysis is running, completed, or failed
Better visibility into analysis queue and processing status
Security implications, and
Recommended next steps for investigation
Conversational interface for direct interaction with the Alert Analyzer agent,
Ability to ask the agent questions about its analysis in real-time,
Dynamic investigation workflows with agent collaboration
Alert Analyzer is designed to integrate with Security Orchestration, Automation, and Response (SOAR) platforms:
Analysis results are returned in JSON format with Markdown-formatted summaries
API endpoints support SOAR playbook integration
Configurable authentication and rate limiting
Optimized response format for automated downstream actions
Results: An average of 45% reduction in manual triage time; faster MTTD and MTTR.
Your AI assistant, built with the instincts of a Tier 3 analyst and trained on thousands of real-world detections, threat behaviors, and triage playbooks.
Monte Copilot is fully integrated with internal and external tools to help you make informed decisions. When you ask a question, Monte Copilot determines which tools to use, queries them, and presents a synthesized answer. You see status updates showing what it's checking as it works.Whether you are investigating an alert, researching a threat, or trying to understand a security event, Monte Copilot provides intelligent assistance to help you work more effectively.
When to use it:
During triage: Paste an encoded PowerShell command and ask for an explanation. Get decoded output with a malicious activity assessment.
See a MITRE ATT&CK technique you don't remember? Ask Monte Copilot to explain it.
Suggest rule improvements or generate new detections on the fly
Parse threat intel reports with more nuance than ChatGPT — and instantly map findings to MITRE TTPs with operational links into your detection armory
Mid-investigation: Stuck on next steps? Describe what you found and ask for suggestions.
Monte doesn’t just talk security, it works like a seasoned analyst.

AI-assisted Triage Case Study
A leading global financial firm faced a growing backlog of security alerts driven by high volumes of false positives and inconsistent triage processes. Analysts were burning out, and the SOC struggled to scale response capacity without expanding headcount.
To tackle this, the firm deployed Anvilogic’s AI-powered Triage Analyzer agent to automate the initial triage process and identify benign activity before it reached human queues.
Traditional detection workflows are:
- Manual and inconsistent: Analysts spent 30–45 minutes per alert, often duplicating work
- Overloaded with false positives: A significant share of alerts were benign but still reviewed manually
- Difficult to prioritize: SOC teams lacked a reliable system to score and tag low-risk activity
AI-powered triage changed that with:
- 45% alert reduction: Nearly half of daily alerts were confidently auto-tagged as benign
- 98% accuracy: AI verdicts on benign alerts were trusted and validated
- L2 workload reduction: Analysts focused on higher-risk alerts without drowning in noise
- Operational lift: Triage fidelity improved, while burnout and backlog decreased
Architecture
.avif)
Product Features:
- Forge Threat Research delivering over 1000s of ready-to-deploy detections (updated weekly) in SPL, KQL, SQL.
- Daily detections updated based on trending threats.
- Premium Threat Scenarios & Cloud Detection Content Packs.
- Hunting detection packs to detect anomalous behavior.
- Low-Code detection builder to create behavior pattern-based detections or risk based detection scenarios.
- Import your pre-existing rules to be standardized across all alert data.
- Frameworks, machine learning recommendations and documentation to help define testing (TTPs) all in one place.
- Automated end-to-end detection lifecycle management.
- Easy to clone/modify/deploy detections.
- Use case documentation.
- Automated maintenance.
- Versioning & audit history of changes.
- Parsing and normalization code management.
- End-to-end visibility of your SOC maturity based on data quality analysis, detection coverage across MITRE, and productivity metrics (ex. hunting, alert dwell time, etc.).
- Measurable technique coverage and gap analysis.
- Assessment validation testing integrated into maturity scoring framework.
- Hunting, Tuning, and Health Insights that continuously monitor your unique environment, escalate activity that requires attention, and remind you of crucial maintenance actions.
- Hunting Insights delivered to help identify high-fidelity alerts and suspicious patterns across raw event logs.
- Detection recommendations based on your industry threat.
- Landscape, infrastructure, and MITRE ATT&CK coverage/gaps.
- Data prioritization & recommendations based on your unique environment.
- Automated Tuning recommendations to ensure your deployment is performing optimally.
- Licensing: annual subscription model based on the user count.
- SaaS Deployment: Meta data, analytics, insights, audit logs, alerts, allowlisting, and enrichment stored in Anvilogic Alert Lake.
- Ability to search, query data, and deploy detections across multiple SIEMs and/or cloud data lakes.
- Able to automatically tag, normalize, and enrich detections before storage for optimal correlation.
- Highly flexible, open API platform that integrates with many existing security technologies.
- Supported Data Platforms: Splunk (On-Prem & Cloud), Azure Data Explorer, Azure Log Analytics, Snowflake (AWS, Azure, GCP).
- SOAR Integrations: Torq, Tines, XSOAR, Swimlane, more.
- Case Management Integrations: Jira, ServiceNow.
- Security Vendor Integrations: Crowdstrike, Proofpoint, Palo Alto Cortex, Tanium, VMware Carbon Black, Microsoft Defender, StackRox, DarkTrace, SentinelOne, ReversingLabs, Hunters, Abnormal Security, and more.
- Alert tuning, allow listing, triage observations.
- Alert triage assisted by the link analysis of the hunting graph.
- Triage across multiple hybrid cloud, cloud, and data lakes.
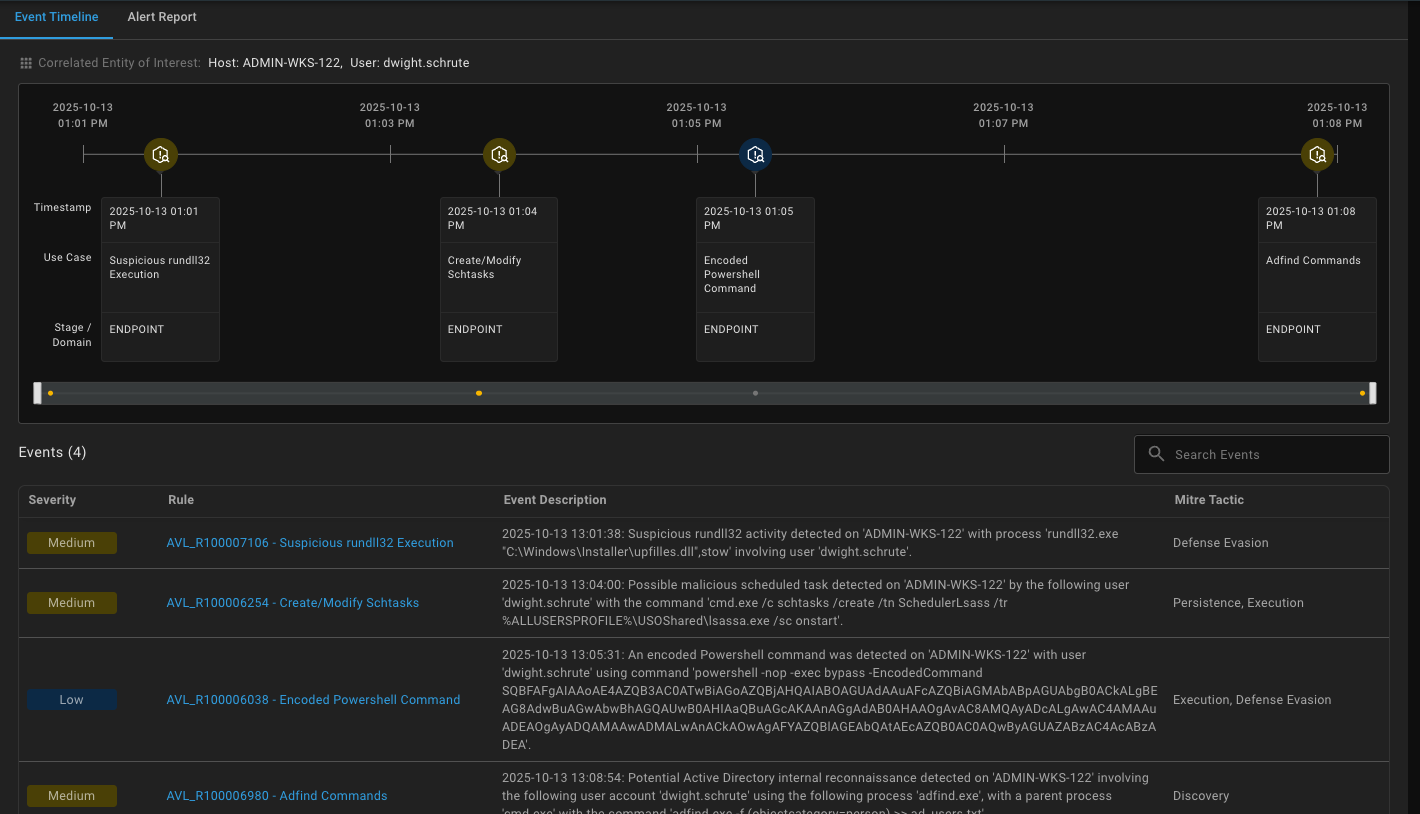
- Visualize alert attack pattern and timeline.
- We supply detections across multiple data repositories, allowing you to easily query different sources and centralize them for seamless correlation in one location.
- SecOps Companion trained across various SOC personas for investigation & detection building assistance.
- Access to common tools and data sets used by analysts for triage ex) VirusTotal, Shodan, IPInfo, and more.





.png)
.png)
.svg)





