Campaign Snapshot: How Makob Gets In and Spreads
Campaign Snapshot: How Makob Gets In and Spreads
Category: Ransomware | Industry: Global | Source: Acronis
Targeting: 55% of observed victims have been in India, with additional cases in Brazil, Germany and others. If you have operations or outsource any part of the biz in these areas double on this coverage, though this as an opportunistic, not country-targeted as attackers go where: RDP is expose, MFA is missing, or patching/EDR posture is weak AF.
- Initial Access TTPs seen
- Exposed RDP is the primary entry point. Attackers have been seen to use brute-force/dictionary attacks against weak or reused credentials, might I remind you of that the Louvres pw to their video surveillance system was literally just Louvre.
- NLBrute specifically was the tool used to perform the above large-scale RDP pasword guessing against exposed RDP port 3389 using un/pw lists. This was an old hacking tool that was being sold on cybercrime forums way back in
- Tool Staging & Lateral Movement
- Makop tooling is most often dropped into:
- RDP-mounted shares like \\tsclient\\*
- Music, Downloads, Desktop, Document user paths.
- Subfolders commonly named Bug or Exp.
- Encryptor file names include:
- bug_osn.exe, bug_hand.exe, 1bugbug.exe, bugbug.exe
- taskmgr.exe, mc_osn,exe plus dot-prefixed variants like .taskmgr.exe
- Makop tooling is most often dropped into:
- For Discovery and Lateral Movement, they rely on the basics
- NetScan (most frequent), but also Advanced IP/Port Scanners, and Masscan
- Used to enumerate hosts, ports, and services and locate high-value systems while blending in with normal admin activity.
Clearly, 3389 gets more unsolicited attention than the hottest kid in school, if it’s open to the internet without MFA and hardening, Makop doesn’t need to look anywhere else. Fix weak RDP folks!
How Makob disables defenses, escalates, and steals creds
Once it's is inside, it doesn’t sprint to encryption, it first cuts the power to your Defender, slips into SYSTEM on the back of dusty CVEs, and then raids every credential stash it can find.
- Defense Evasion
- AV Killers / Defender tampering:
- BYOVD (Bring Your Own Vulnerable Driver):
- hlpdrv.sys and ThrottleStop.sys:
- ThrottleStop.sys is a legitimate signed driver (CVE-2025-0771) abused for memory access to disable security tools.
- hlpdrv.sys can gain kernel-level access and terminate EDR services.
- These drivers have also been seen with MedusaLocker, Akira, & Qilin.
- Region-specific AV removal:
- A tailored Quick Heal AV uninstaller is used to remove Quick Heal (popular in India), matching the observed victim geography of this trending threat.
- Abuse of other legit tools:
- Process Hacker and IOBitUnlocker are used to terminate processes and remove locked files.
- BYOVD (Bring Your Own Vulnerable Driver):
- Defender Control and Disable Defender to turn off Microsoft Defender Protections
- Keep in mind: we have several defendar impair defense detections in the armory make sure they are actively deployed.

- Privilege EscalationMakop brings a pack of Windows local privilege escalation (LPE) exploits, many with public PoCs and reliable SYSTEM access:
Makop brings a pack of Windows local privilege escalation (LPE) exploits, many with public PoCs and reliable SYSTEM access:
- CVE-2016-0099
- CVE-2017-0213
- CVE-2018-8639
- CVE-2019-1388
- CVE-2020-0787
- CVE-2020-0796
- CVE-2020-1066
- CVE-2021-41379
- CVE-2022-24521
- These target BITs, Win32k, SMB/KS drivers, Windows Installer, vendor IOCTL, etc.
- Credential Access
Mimikatz dumps:
- LaZange
- browsers, Wi-Fi profiles, email clients, databases and windows credential stores.
- NetPass
- mapped drives, VPNs, RDP sessions, other windows networking secrets.
- Brute-Force Tools:
- CrackAccount and AccountRestore try multiple password combinations to compromise additional accounts.
- plaintext passwords, NTLM hashes, Kerberos tickets and other LSA-managed secrets.
Net result: disabled AV, reliable privilege escalation, and a full credential grab that results in the perfect setup for a low-friction ransomware deployment
Payload delivery shift: GuLoader + Makop and detection priorities
Net New Pattern: GuLoader Integration (tactical evolution)
Makop is now observed using GuLoader as a delivery mechanism – a meaningful shift from “just drop the encryptor” to staged loader-based delivery.
- GuLoader is a downloader trojan (since 2019) known to deliver:
- AgentTesla, FormBook, Xloader, Lokibot, etc.
- In Makop incidents, the following activity was seen GuLoader do:
- dropped in the same directory as other others (e.g., under Music\1\BUG\)
- used to fetch and execute Makop encryptors
- dropped in the same directory as other others (e.g., under Music\1\BUG\)
Example execution chain:
- "%USERPROFILE%\Music\1\BUG\TreasureRoberts.exe"
- Executes GuLoader, drops a VBS script.
- "%WINDIR%\System32\WScript.exe" "%USERPROFILE%\Music\1\BUG\67138435cf99c.vbs"
- Guloader deploys Makop variants
Detection priority themes
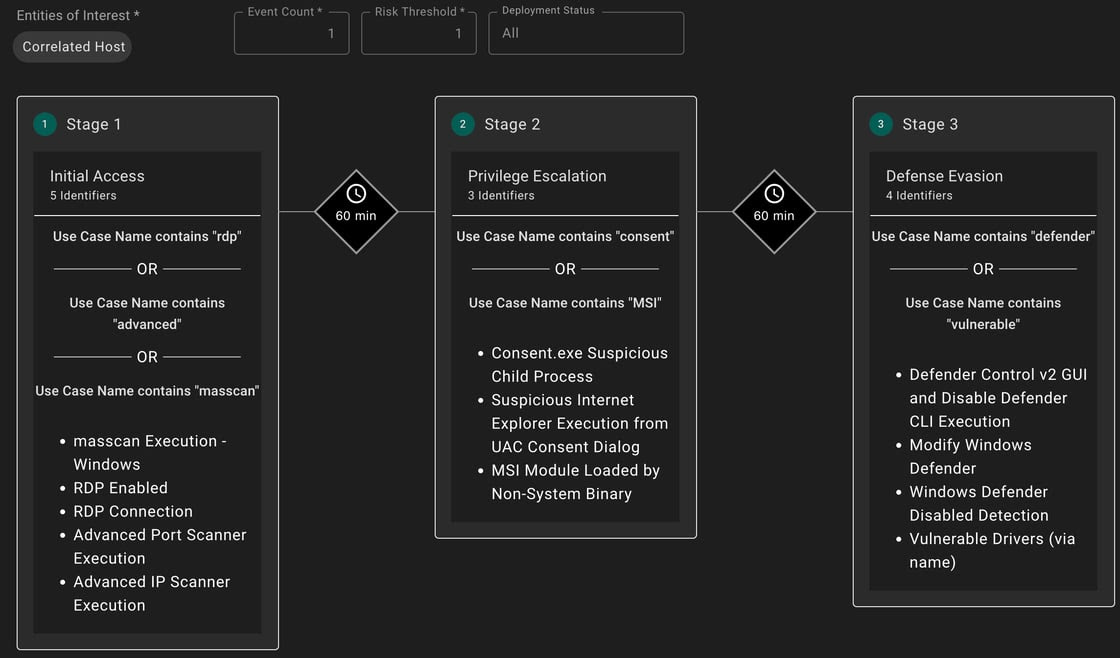
When you hook this into Anvilogic detections, the three big buckets above translate into:
- RDP & Staging Activity
- Internet-exposed RDP + brute forcing (NLBrute behavior, failed logons)
- Suspicious file drops and process executions from \\tsclient\, Music, Downloads, Desktop, Documents, C:\, especially Bug / Exp folders and bug*/mc*/taskmgr.exe names.
- Network/port scanning from user endpoints and non-admin infrastructure.
- Defense & Privilege tampering
- Defender being disabled via tools or registry/service changes.
- Loading of vulnerable drivers (hlpdrv.sys, ThrottleStop.sys) and AV uninstall activity (Quick Heal).
- LPE exploit tooling observed shortly before SYSTEM-level activity.
- Credential theft & GuLoader = Ransomware chain
- Execution of Mimikatz, LaZagne, NetPass, CrackAccount, AccountRestore.
- WScript executing VBS from paths like Music\1\BUG\*.vbs followed by .mc_* Makop binaries.
- Any loader-like behavior (GuLoader patterns) followed by encryption or mass file access.








.png)


.svg)





